Table of Contents
Before starting Google hacking let me make it clear what I mean by Google hacking!
What is Google hacking?
Google hacking involves using the advanced operator in the Google search engine to extract useful information that a normal user can’t extract from a website.
Let me make it clearer, Google hacking doesn’t mean that we are going to hack the Google websites but it means that we are using certain operators that are provided by Google to narrow down search or search more efficiently.

These operators are also known as “Google Dorks” and can be used by hackers.
Don’t know how hackers use Google dorks then so, here I am going to explain to you how hackers use Google Dorks to create complex queries and extract information that a normal user can’t extract from a particular website.
I hope you have got clear idea of Google hacking and Google dorks
Here I have listed some of the most Basic Dorks and how they are used:
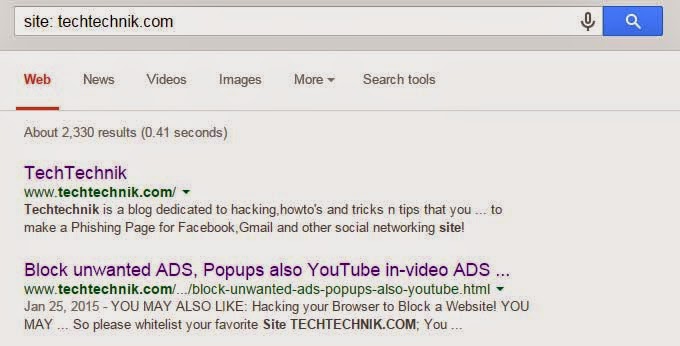
1) Site:
It restricts the search results to a specific domain only that is when it is used it will return all the pages and sub-domains of the specific Domain.
Syntax: site: domain name
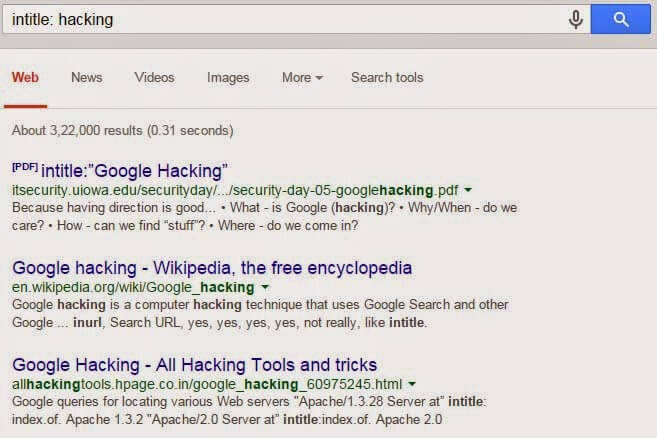
2) intitle:
3) allintitle:
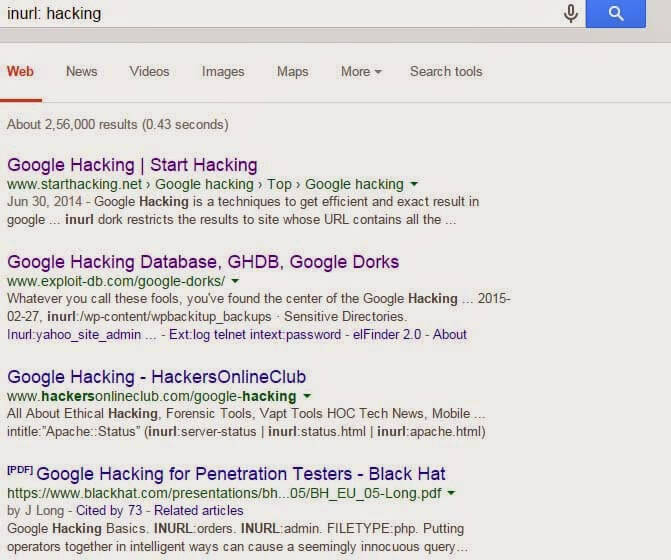
4) inurl:
5) allinurl:
It’s almost similar to the inurl dork.The only difference between allinurl and inurl is that allinurl will restrict the results to display all the keywords or collection of keywords in the url whereas inurl is used to narrow search only for specific single keyword in the url.
syntax: allinurl: keyword
6) related:
7) cache:
It will display all the cached version of a website or webpages that is kept with Google
Syntax: cache: www.domain name
cache: www.tectechnik.com will return the cached version of techtechnik.com.
8) ext or filetype:
It will show all the sites that contain specific filetype.
Syntax: ext: extension of file type
ext: pdf hacking will return the hacking sites which have pdf files in them.
9) intext:
It will show all the sites that have a specific word or text in there page.
Syntax: in text: text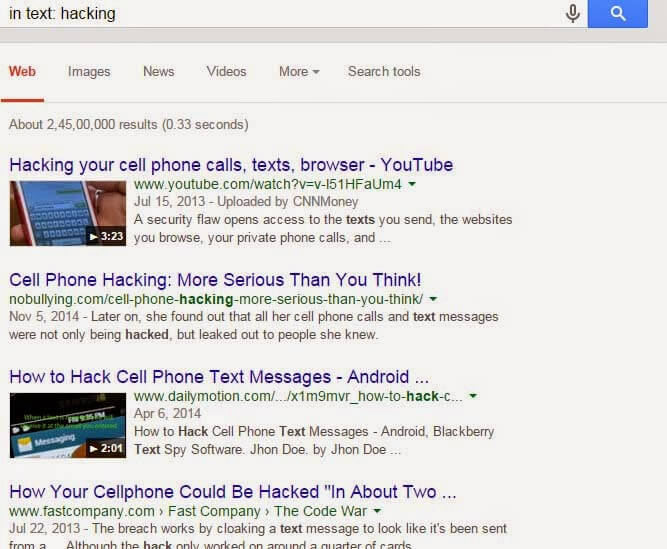
in text: hacking will return all the websites that have hacking text in there pages.
10) +:
It is used to display the series of text .
syntax: word1+word2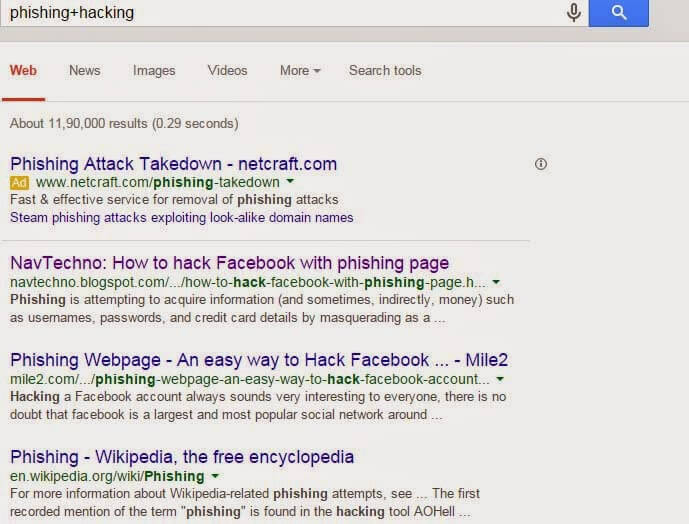
phishing+hacking will display all the result that contain both words i.e phishing and hacking.
These Dork’s when used wisely are really helpful to hackers as they can use dorks to find the vulnerable sites!
Here is a video that will help you understand the usability of Google Dorks more clearer:
[su_youtube url=”https://www.youtube.com/watch?v=iIIuG7Xt_PQ”]
Now let’s use Dorks from a Hackers point of view:
So hacker will write inurl:adminlogin and hacker will get tons of site with admin page login.
Now let us find the admin page of the particular website
Let us use site:facebook.com inurl:login
In the above dork we have combined two dorks site and inurl ,it will give the login page of the facebook, as facebook restricts the display of the admin login page. and you can try other websites to get admin page.
Let us use some complex Google dorks intext:”Hikvision” inurl:”login.asp”
the above link will give us the login page of the of hikvision cameras which are used as CCTV.
And in the similar way hackers combines different Google dorks to get all the sensitive information of different vulnerable sites..
Here are list of some Google dorks you can play with:
1.“Index of /admin”
2. “Index of /password”
3. “Index of /mail”
4. “Index of /” +passwd
5. “Index of /” +password.txt
6. “Index of /” +.htaccess
7. index of ftp +.mdb allinurl:/cgi-bin/ +mailto
8. administrators.pwd.index
9. authors.pwd.index
10. service.pwd.index
11. filetype:config web
12. gobal.asax index
13. allintitle: “index of/admin”
14. allintitle: “index of/root”
15. allintitle: sensitive filetype:doc
16. allintitle: restricted filetype :mail
17. allintitle: restricted filetype:doc site:gov
18. inurlasswd filetype:txt
19. inurl:admin filetype:db
20. inurl:iisadmin
21. inurl:”auth_user_file.txt”
22. inurl:”wwwroot/*.”
23. top secret site:mil
24. confidential site:mil
25. allinurl: winnt/system32/ (get cmd.exe)
26. allinurl:/bash_history
27. intitle:”Index of” .sh_history
28. intitle:”Index of” .bash_history
29. intitle:”index of” passwd
30. intitle:”index of” people.lst
31. intitle:”index of” pwd.db
32. intitle:”index of” etc/shadow
33. intitle:”index of” spwd
34. intitle:”index of” master.passwd
35. intitle:”index of” htpasswd
36. intitle:”index of” members OR accounts
37. intitle:”index of” user_carts OR user_cart
Google Dorks can be effectively used to unlock google’s power,however hackers can also use Google dorks for hacking into vulnerable accounts so its always safe to put a strong password for your account…!!!